Introduction
Secure communication and billing are significant concerns for various businesses relying on VoIP for communication requirements. However, there is another dark side of VoIP that is quite daunting for companies. And that is VoIP fraud. VoIP fraud is the network's vulnerability, making it prone to theft, DDoS attacks, spamming, and many other issues.What is VoIP Fraud?
VoIP fraud occurs when attackers use VoIP networks' security flaws to place unauthorized calls or get access to confidential data. It is an unauthorized use of paid communication services charged to a party that isn't expecting it. The party can be customers or service providers.In other words, this can cost your firm or a fortune from which it might be challenging to recover. The hacker will profit from you or your client, who will pay the price.
Though not new, VoIP fraud is becoming more prevalent. According to the Communications Fraud Control Association (CFCA), telecom unethical practices costed $28.3 billion in 2019. This figure makes up a sizable share of cyber attacks. Hackers frequently try to get around paying service provider fees or get someone else to cover the debt.
The VoIP session border controller manages all these vulnerabilities and secures the IP network from all possible VoIP frauds.
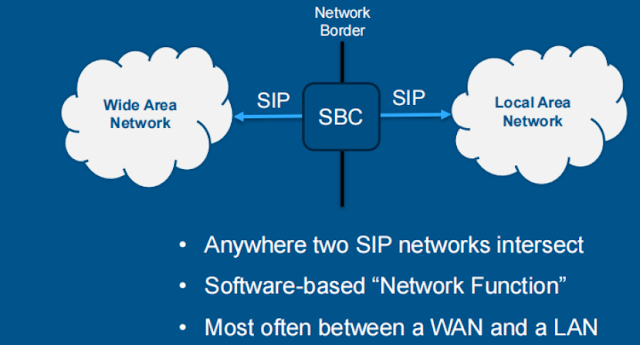
What is a Session Border Controller (SBC)?
A session border controller is a powerful network element that protects SIP-based VoIP networks. One of the primary goals of incorporating SBC in the VoIP network is to handle security issues. Since the internet can be a vulnerable space to place calls, securing the sessions over IP is crucial.SBCs are placed on VoIP networks or the Public Switched Telephone Network (PSTN) to connect to a network or at the network's edge. VoIP session border controllers are necessary for protecting VoIP networks since they carry out various crucial tasks.
Many of you may have a general question: Can the firewall replace SBC?
The answer is NO. A firewall protects the data network. However, it has certain limitations as well. A firewall does not render protection against application layer attacks, overload traffic, account theft, and smart sniffing.
Now Let us understand,
How does VoIP SBC prevent VoIP Fraud?
VoIP SBC Solutions offer an extra layer of protection to the IP network. It offers encryption and defense against specialized attack protection, for instance, packet identification, validity, behavior analysis, and traffic control. It also takes care of,- Access Control.
- Routing
- Signaling Media
- Qos and Data Conversion
Let us understand in detail -
1. Authentication
Authentication, as the name implies, is verifying the identity. SBC confirms the calling party's identity and credentials to place the calls. A session border controller uses a funnel like a database, biometric authentication, or multi-factor authentication to boost VoIP network security further. This step is crucial as it prevents spoofing attacks where attackers forge their identity to place unauthorized calls.2. Encryption
Encryption restricts unauthorized access to sensitive information by transforming the message into a cryptic form. SBC VoIP uses protocols like SRTP (Secure Real-Time Transport Protocol) for voice and video transmission, making it far more challenging for hackers to intercept and steal private data.SRTP protocol offers message encryption, authentication, and integrity. It also prevents eavesdropping and interception. That's how VoIP SBC Solutions take preventive measures against VoIP frauds.
3. Reporting and Monitoring
To help find potential threats and weaknesses, SBCs can monitor VoIP traffic and produce reports. To recognize irregularities in network traffic, they might monitor call volumes, call durations, and other indicators.When SBC detects suspicious activity, VoIP SBC produces alerts. It helps network administrators or security teams receive these notifications and take immediate action in the event of a threat.

No comments:
Post a Comment